Record🤔
cid:
"bafyreiel6v5qntnopsqbutodalys65gcu75jl7ytjloa76xygp3akza3ra"
value:
$type:
"app.bsky.feed.post"
embed:
$type:
"app.bsky.embed.images"
images:
alt:
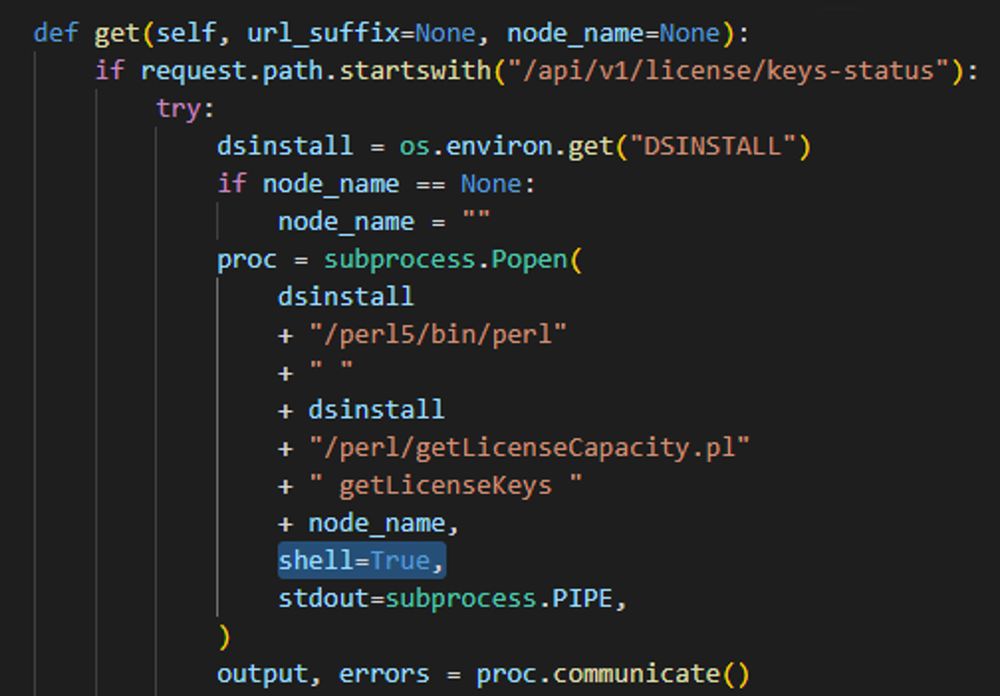
"def get(self, url_suffix=None, node_name=None): if request.path.startswith("/api/v1/license/keys-status"): try: dsinstall = os.environ.get("DSINSTALL") if node_name == None: node_name = "" proc = subprocess.Popen( dsinstall + "/perl5/bin/perl" + " " + dsinstall + "/perl/getLicenseCapacity.pl" + " getLicenseKeys " + node_name, shell=True, stdout=subprocess.PIPE, ) output, errors = proc.communicate()"image:
View blob content
$type:
"blob"
mimeType:
"image/jpeg"
size:
296490
aspectRatio:
width:
1008
height:
702
alt:
"Security Considerations Unlike some other popen functions, this implementation will never implicitly call a system shell. This means that all characters, including shell metacharacters, can safely be passed to child processes. If the shell is invoked explicitly, via shell=True, it is the application’s responsibility to ensure that all whitespace and metacharacters are quoted appropriately to avoid shell injection vulnerabilities. On some platforms, it is possible to use shlex.quote() for this escaping."
image:
View blob content
$type:
"blob"
mimeType:
"image/jpeg"
size:
185835
aspectRatio:
width:
944
height:
444
langs:
"en"
createdAt:
"2024-01-18T17:55:24.682Z"